If you are searching about Public Key Cryptography Explained | Sectigo® Official you've came to the right page. We have 15 Pictures about Public Key Cryptography Explained | Sectigo® Official like Assignment Hub: Encryption_Decryption in C, The Complete Cryptography Guide - Asymmetric vs. Symmetric Encryption and also Key Secure – Encryption Key Management - אינפוגארד. Here it is:
Public Key Cryptography Explained | Sectigo® Official
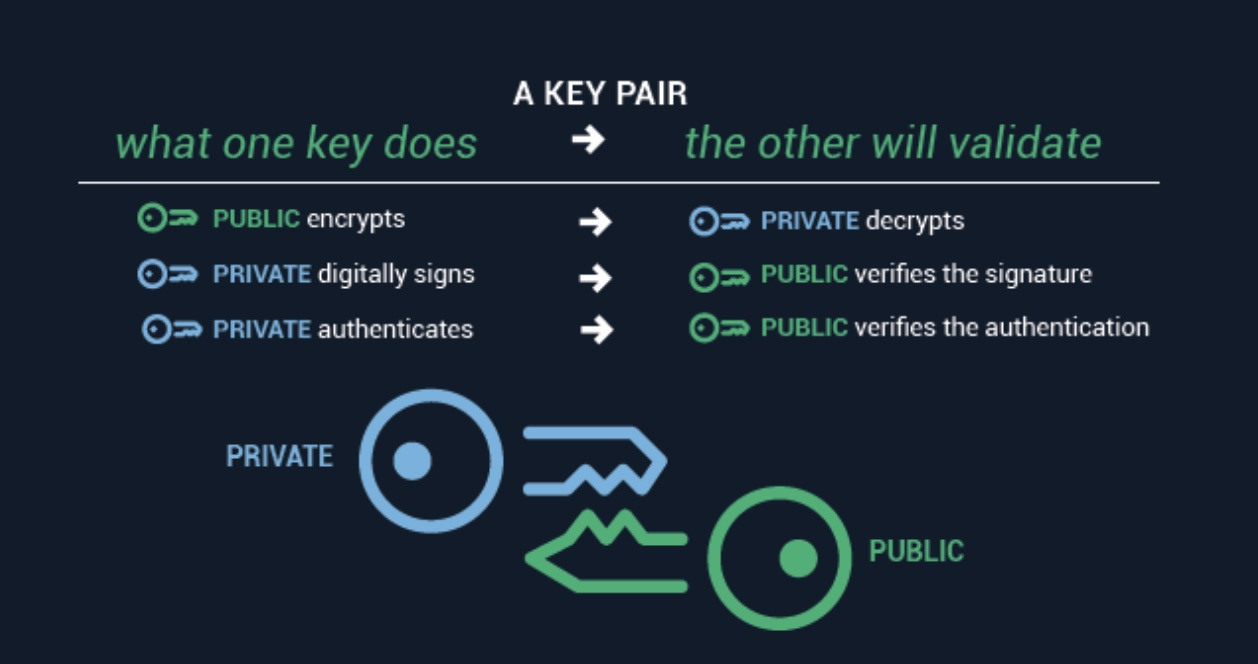 sectigo.com
sectigo.com cryptography explained sectigo
How Do I Create Encryption Keys And Encryption Key Groups And Then
key support keys encryption then clicking button
How To Encrypt Keyboard To Avoid Keyloggers - YouTube
 www.youtube.com
www.youtube.com How To Encrypt Keyboard To Avoid Keyloggers (Best Protection Solution
 www.androidtrickshindi.com
www.androidtrickshindi.com Recover Bitlocker Recovery Key | Password Recovery
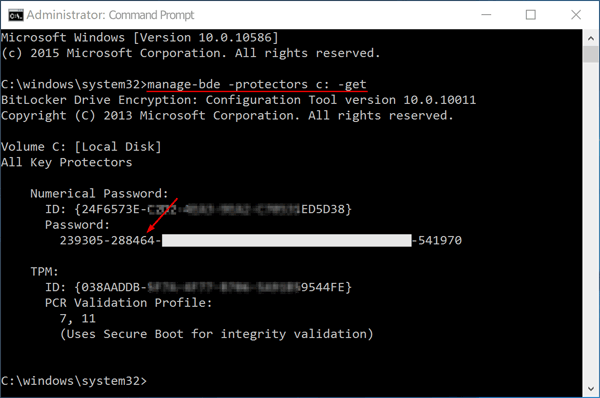 www.top-password.com
www.top-password.com bitlocker recovery key recover password surface pro cmd enter manage bde command windows drive screen microsoft account server user ways
Generating An Encryption Key Without A Pass Phrase — Meet ECIES | By
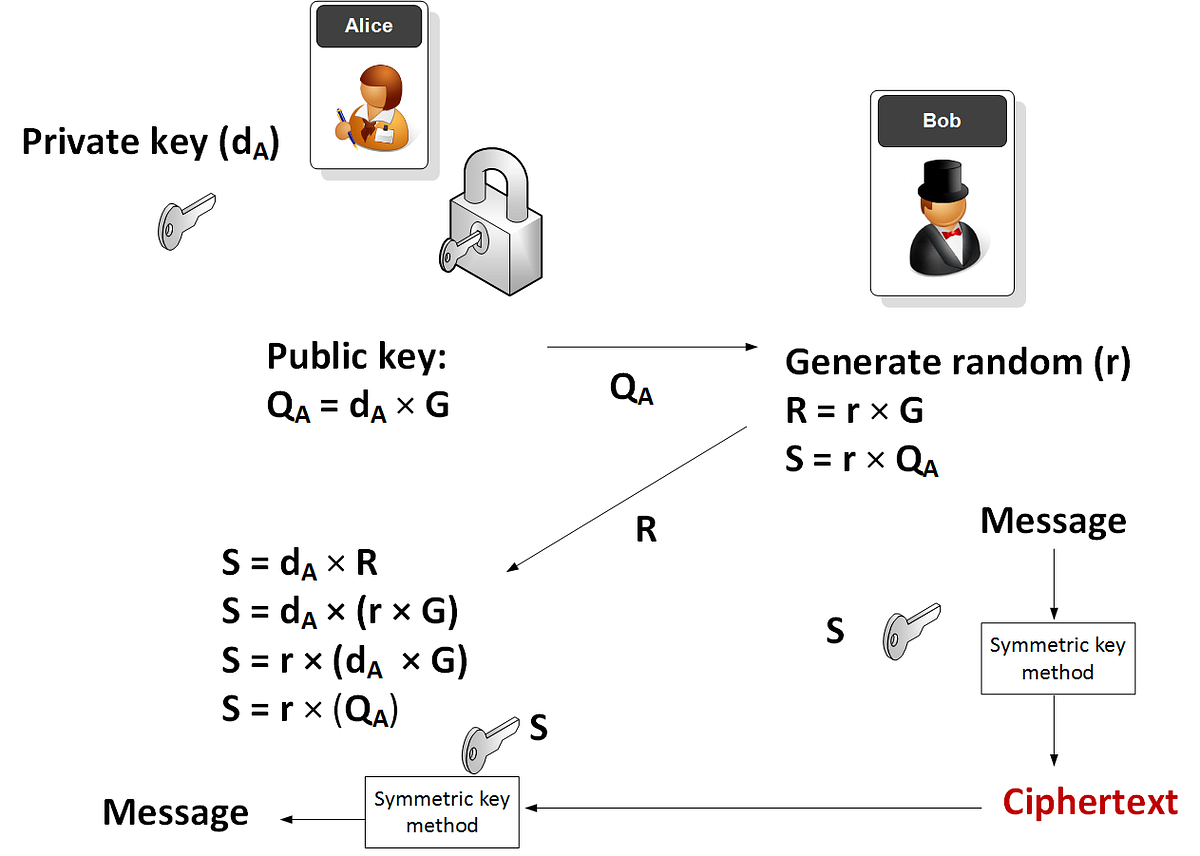 medium.com
medium.com encryption key generating sample medium meet phrase pass without alice bob
The Complete Cryptography Guide - Asymmetric Vs. Symmetric Encryption
 academy.ivanontech.com
academy.ivanontech.com encryption cryptography schermo symmetric crittografia codici testi keamanan jaringan cryptographic chiave indirizzi videoconferenza lifesize livello scientists techprate memakai enkripsi impresacity
Encryption Key Royalty Free Stock Photography - Image: 7785717
key encryption encrypted royalty dreamstime
Caesar Cipher Hackerrank Algorithm Solution In Java - Brighter API
 brighterapi.com
brighterapi.com cipher caesar algorithm worksheet java hackerrank question answers
Hotel Key Card - RFID Room Cards, Hotel Key Cards Manufacturer Supplier
 www.smartcardchn.com
www.smartcardchn.com key card hotel cards
Assignment Hub: Encryption_Decryption In C
 assignmenthub12.blogspot.com
assignmenthub12.blogspot.com encryption key decryption assignment hub matching
Key Secure – Encryption Key Management - אינפוגארד
 www.infoguard.co.il
www.infoguard.co.il Know Your Tech: Encryption Key - Casserly Consulting
 www.casserlyconsulting.com
www.casserlyconsulting.com encryption key tech know
Key Lock Icon | Line Iconset | IconsMind
lock key icon icons outline unlock line handshake security iconsmind access open icns ico file iconarchive
Encryption Key Creation - KA Industries, Inc –You Own The Key : KA
 kaindustries.com
kaindustries.com encryption
How to encrypt keyboard to avoid keyloggers (best protection solution. Encryption key royalty free stock photography. Cipher caesar algorithm worksheet java hackerrank question answers